OSINT Alert & Control Console
OSINT Alert & Control Console provides automated, continuous monitoring of your organization’s external digital footprint.
REQUEST A DEMOGET DATA SHEETOrganizations are investing more in OSINT teams and tools to quickly distill content from thousands of ever-changing internet locations and prioritize responses to threats and content discovered at those sites.
Hunter is the go-to platform for continuous monitoring of all OSINT channels. Dome’s versatility extends to both investigative and protective use cases, tracking Persons of Interest, monitoring Topics of Interest, linking Groups of Interest, tracking Common Vulnerabilities and Exposures (CVE) chatter, analyzing Supply Chain risks, Portfolio Management, supporting continuous monitoring for SOC Investigations, and continuous Reputation Monitoring & Protection.
Hunter Alert Console equips organizations with the tools to proactively protect their digital presence, defend against threats, and maintain their reputation in the ever-evolving online world. Hunter distills content from the surface web, social media, deep web, and dark web into a single view, backed by an industry-leading rules-based threat model, allowing customers full control over collection and risk ranking/prioritization.
Key Features:
- Easy Configuration and Operation: User-friendly and quick to operationalize within customer environments.
- Reduce False Positives: Customize advanced policies and disambiguation rules to reduce false alarms.
- Mitigation and Respond: Report and initiate the removal of harmful data, including takedown capabilities.
- Unmask Source of Smears and Attacks: Query the original source and attribute the group or individual behind the suspicious or malicious activity.
Comprehensive Protection Against External Risk
Unified Platform Speeds Response – Eliminate the siloes of data and ad hoc processes that delay response to risks outside your perimeter.
- Automated Monitoring: Continuous monitoring of external risks eliminates manual OSINT collection that consumes your staff’s valuable time.
- ML-Powered Analysis: Machine learning delivers faster access to critical insights and reduces your mean time to response (MTTR).
- Unmatched Scalability: Unlimited scalability and rapid onboarding enable you to protect any size organization quickly.
- Improve OSINT analyst productivity: Let your analysts focus on analyzing relevant content, not managing VPNs, ToR browsers and spreadsheets of URLs to manually track.
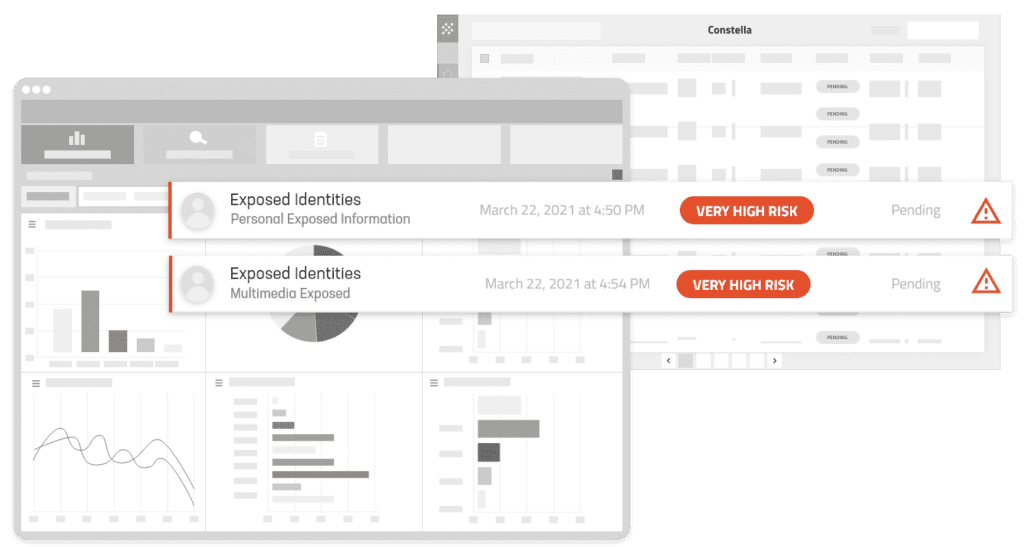
Public & Proprietary Data Delivers Comprehensive Intelligence
Enterprise-Wide Visibility – Know the scope of your external risks with continuous analysis of thousands of data sources and billions of data points.
Threat Landscape Awareness
Automates monitoring of the Surface, Deep, and Dark Web, Social Media, messaging apps, data brokers, phishing, and botnet attacks.
Curated, Accurate Data
Leverages the industry’s largest curated collection of compromised identities, with over 124B identity records and 180B attributes spanning 15+ years.
Embedded Expertise
Eliminates reliance on in-house staff or specialized skills to know where to find malicious activity and content.
Operationalize Digital Risk Protection
Built-in integrations with your provisioning systems, security tools, and response workflows make existing teams and processes more effective.
Enhanced Threat Response
Increase SIEM, SOAR, and TIP effectively by incorporating external risk intelligence.
Faster Onboarding
Quickly onboard and auto-provision executives or employees via Active Directory integration.
Accelerated Response
Streamline ticketing workflows and eliminate manual processes with ServiceNow integration.
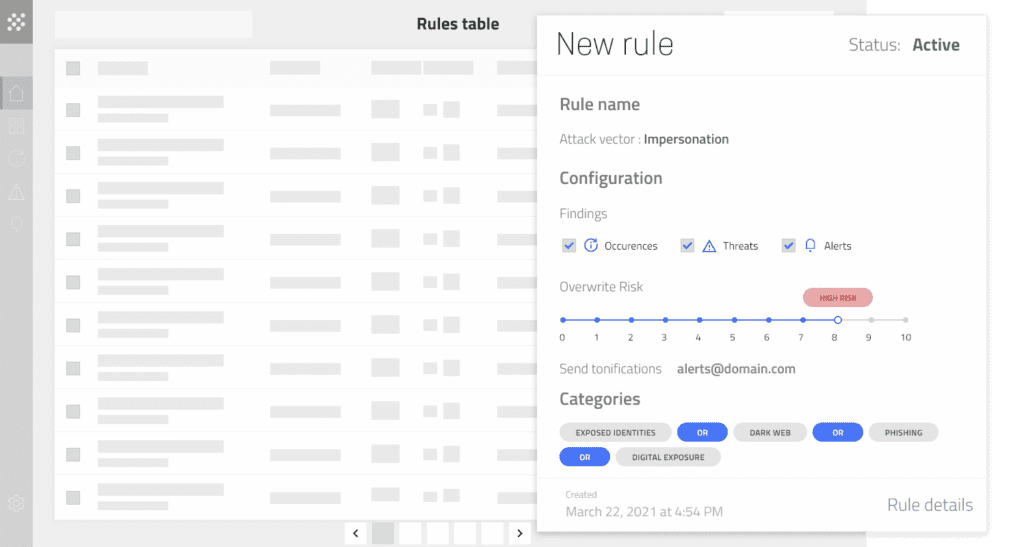
Eliminate Noise with Customizable Threat Models
Tune Hunter’s threat models to reduce alert overload and false positives
- Modify the policies to fit your unique requirements.
- Receive only the information you need, when you need it.
- Eliminate low-value alerts that consume scarce resources.
Constella.ai is the global leader in AI-driven identity risk and deep and dark web intelligence for such applications as identity theft, insider risk, synthetic identity fraud detection (Advanced KYE/KYB), and deep OSINT investigations.
With the world’s largest breach database, containing over one trillion data attributes in 125+ countries and over 53 languages, Constella empowers leading organizations across the globe to monitor and secure critical data through unparalleled visibility and actionable insights.
Digital Risk Protection Platforms
Executive and Brand Digital Protection
Subscribe To The Constella Newsletter
©2025 Constella Intelligence. All rights reserved. Website Privacy Policy. Terms of Use. Datalake Privacy Notice. Acceptable Use Policy.



